Most of you guys must have logged onto servers using SSH protocol and verified yourself with a Password. Everything seems good, but don’t you sometimes feel a bit frustrated when every-time you have to enter the password, also entering the password is not the best way in terms of security (storing a password in scripts which auto logins to a server is not a good idea). That’s where the concept of SSH Keys comes into the picture.
‘SSH keys’ is one of the many ways of authenticating, while logging to a remote server over the internet. SSH keys work on the principle of Asymmetric cryptography where client and server have different keys and authentication is successful as long as these 2 keys fit the formula (as both of these keys are derived from a mathematical formula). Now we will see how to use SSH keys as a method of authentication.
STEP 1: Generate an SSH key pair
ssh-keygen -t rsa
This command will generate 2 keys under a hidden folder named ‘.ssh/‘ in your home directory. Before generating new keys its best to check if any previous keys are present (cd ./ssh)
The 2 generated keys are as follows :
PUBLIC KEY (id_rsa.pub): This key is given to the system (server) to which we are trying to connect.
PRIVATE KEY (id_rsa): This key is stored on the system from which we are trying to connect.
STEP 2: Upload the Public key on Server
Now you need to upload the Public Key to the server to which your client will connect. eg: while configuring ssh keys on Github we paste the public key in Github’s ssh keys settings.
ssh-copy-id root@172.20.10.2
ssh-copy-id uses the SSH protocol to connect to the target host and upload the SSH user key. This command edits the authorized_keys file on the server. It creates the .ssh directory if it doesn’t exist. It creates the authorized keys file if it doesn’t exist. Effectively, copying the public key to the server.
STEP 3: Connecting to the Server
When the client tries to connect to the server, below sequence of operations take place
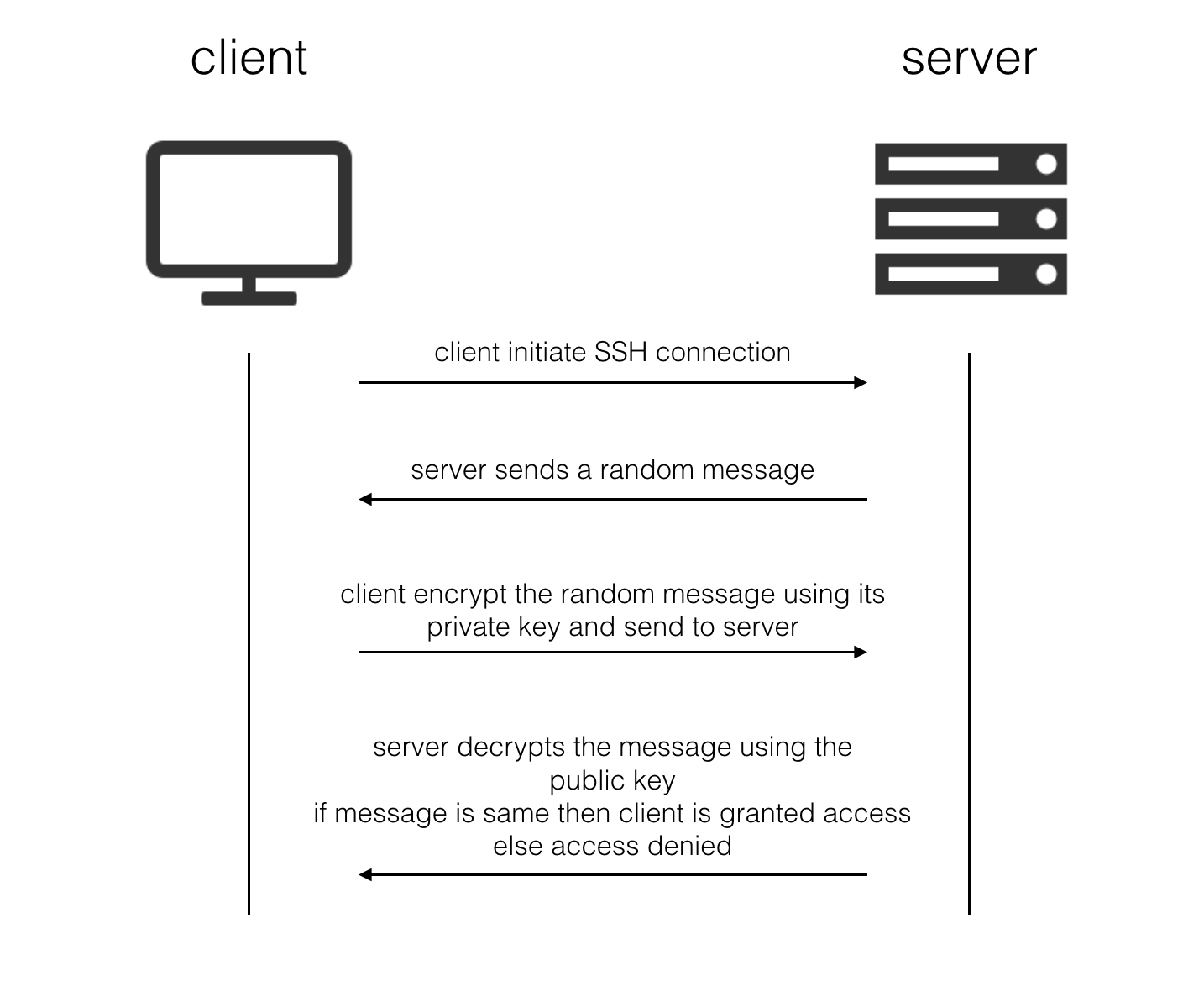
This creates an authentication mechanism based on “something you have” (the private key file) as opposes to “something you know” (a password or phrase). The best authentication mechanisms contain a component of both – this is why ssh-keygen prompts you for a passphrase to encrypt the private key.
NOTE: After the client is authenticated by the server an SSH tunnel is established. The data send over SSH is encrypted with a session key(which is shared between client and server after establishing the connection). Also, the session key uses a symmetrical cryptography technique.
